SET-W NEXT-->
1.
Break-down in verbal communication is described as
(A) Short
circuit (B) Contradiction (C) Unevenness (D) Entropy
2.
The Telephone Model of Communication was first developed in the
area of
(A)
Technological theory (B) Dispersion
theory
(C) Minimal
effects theory (D) Information theory
3.
The Dada Saheb Phalke Award for 2013 has been conferred on
(A) Karan
Johar (B) Amir Khan (C) Asha Bhonsle (D) Gulzar
4.
Photographs are not easy to
(A) publish
(B) secure (C) decode (D) change
5.
The grains that appear on television set when operated are also
referred to as
(A)
sparks (B) green dots (C) snow (D) rain drops
6.
In circular communication, the encoder becomes a decoder when
there is
(A) noise (B)
audience (C) criticality (D) feedback
7.
In a post-office, stamps of three different denominations of `
7, ` 8, `
10 are available. The exact amount for which one cannot buy stamps
is
(A) 19 (B) 20 (C)
23 (D) 29
8.
In certain coding method, the word QUESTION is encoded as DOMESTIC.
In this coding, what is the code word for the word RESPONSE ?
(A) OMESUCEM (B) OMESICSM (C) OMESICEM (D)
OMESISCM
9.
If the series 4, 5, 8, 13, 14, 17, 22, .... is continued in the
same pattern, which one of the following is not a term of this series ?
(A) 31 (B) 32 (C)
33 (D) 35
10.
Complete the series BB, FE, II, ML, PP, ...........by choosing one
of the following option given :
(A) TS (B) ST (C)
RS (D) SR
11.
A man started walking from his house towards south. After walking
6 km, he turned to his left and walked 5 km. Then he walked further 3 km after turning
left. He then turned to his left and continued his walk for 9 km. How far is he
away from his house ?
(A) 3 km (B) 4
km (C) 5 km (D) 6 km
12.
One writes all numbers from 50 to 99 without the digits 2 and 7.
How many numbers have been written ?
(A) 32 (B) 36 (C)
40 (D) 38
13.
“If a large diamond is cut up into little bits, it will lose its
value just as an army is divided up into small units of soldiers, it loses its
strength.” The argument put above may be called as
(A) Analogical
(B) Deductive (C) Statistical (D) Causal
14.
Given below are some characteristics of logical argument. Select
the code which expresses a characteristic which is not of inductive in
character.
(A) The
conclusion is claimed to follow from its premises.
(B) The
conclusion is based on causal relation.
(C) The
conclusion conclusively follows from its premises.
(D) The
conclusion is based on observation and experiment.
15.
If two propositions having the same subject and predicate terms
can both be true but can not both be false, the relation between those two propositions
is called
(A)
contradictory (B) contrary (C) subcontrary (D) subaltern
16.
Given below are two premises and four conclusions drawn from those
premises. Select the code that expresses conclusion drawn validly from the
premises (separately or jointly).Premises :
(a) All dogs
are mammals. (b) No cats are dogs.
Conclusions
:
(i) No cats
are mammals. (ii) Some cats are mammals.
(iii) No dogs
are cats. (iv) No dogs are non-mammals.
Codes
:
(A) (i) only
(B) (i) and (ii)
(C) (iii) and
(iv) (D) (ii) and (iii)
17.
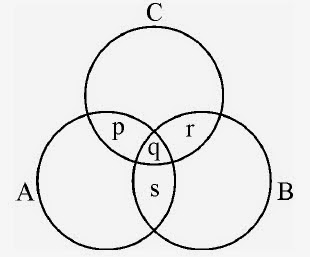
Given below is a diagram of three circles A, B & C
inter-related with each other. The circle A represents the class of Indians,
the circle B represents the class of scientists and circle C represents the
class of politicians. p, q, r, s ... represent different regions. Select the
code containing the region that indicates the class of Indian scientists who
are not politicians.
Codes
:
(A) q and s
only (B) s only (C) s and r only (D) p, q and s only
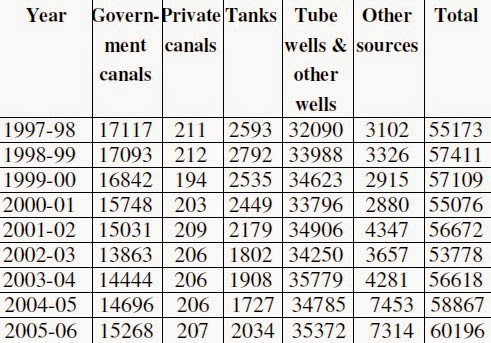
Read the
following table carefully.Based upon this table answer question from 18
to 22 :
18.
Which of the following sources of Irrigation has registered the
largest percentage of decline in Net area under irrigation during 1997-98 and
2005-06 ?
(A) Government
canals (B) Private canals (C) Tanks (D) Other sources
19.
Find out the source of Irrigation that has registered the maximum
improvement
in terms of
percentage of Net irrigated area during 2002-03 and 2003-04.
(A) Government
canals (B) Tanks
(C) Tube wells
and other wells (D) Other sources
20.
In which of the following years, Net irrigation by tanks increased
at the highest rate ?
(A) 1998-99
(B) 2000-01 (C) 2003-04 (D) 2005-06
21.
Identify the source of Irrigation that has recorded the maximum
incidence of negative growth in terms of Net irrigated area during the years
given in the table.
(A) Government
canals (B) Private canals
(C) Tube wells
and other wells (D) Other sources
22.
In which of the following years, share of the tube wells and other
wells in the total net irrigated area was the highest ?
(A) 1998-99
(B) 2000-01 (C) 2002-03 (D) 2004-05
23.
The acronym FTP stands for
(A) File
Transfer Protocol (B) Fast Transfer
Protocol
(C) File
Tracking Protocol (D) File Transfer
Procedure
24.
Which one of the following is not a/an image/graphic file format ?
(A) PNG (B)
GIF (C) BMP (D) GUI
25.
The first web browser is
(A) Internet
Explorer (B) Netscape (C) World Wide Web (D) Firefox
26.
When a computer is booting, BIOS is loaded to the memory by
(A) RAM (B)
ROM (C) CD-ROM (D) TCP
27.
Which one of the following is not the same as the other three ?
(A) MAC
address (B) Hardware address
(C) Physical
address (D) IP address
28.
Identify the IP address from the following :
(A) 300 × 215
× 317 × 3 (B) 302 × 215@
417 × 5
(C) 202 × 50
× 20 × 148 (D) 202 – 50 – 20 – 148
29.
The population of India is about 1.2 billion. Take the average
consumption of energy per person per year in India as 30 Mega Joules. If this consumption
is met by carbon based fuels and the rate of carbon emissions per kilojoule is
15 × 106 kgs, the total carbon emissions per year from
India will be
(A) 54 million
metric tons (B) 540 million metric
tons
(C) 5400
million metric tons (D) 2400 million
metric tons
30.
Which of the following cities has been worst affected by urban
smog in recent time?
(A) Paris (B) London
(C) Los Angeles (D) Beijing